Firewalls
A network firewall acts as a filter for network traffic to and from resources in a virtual network. It contains rules that govern inbound and outbound traffic for virtual machines, allowing or denying access based on properties such as the direction of traffic, source or destination IP, protocol, ethertype, and port range.
Firewall rules are the building blocks of firewalls. Each rule specifies the conditions under which network traffic is allowed or denied. Firewalls, which contain one or more rules, can be attached to virtual machines to enforce these security policies. Alternatively, direct firewall rules can be applied to individual virtual machines for more specific configurations.
Each firewall rule specifies the following properties:
- Direction: Each firewall rule applies to incoming (ingress) or outgoing (egress) connections, not both.
- Source or destination: Firewall rules support IPv4 or IPv6 connections.
- Protocol: The protocol to allow. The most common protocols are TCP, UDP, and ICMP.
- Port range: The range of ports to allow. You can specify a single port number (for example, 22), or a range of port numbers (for example, 7000-8000).
Take control of your virtual machine's security by configuring firewalls to specify which ports are open to the public, thereby protecting your resources. To ensure security, designate only the necessary ports for ingress and egress traffic, as by default, no external communication with your virtual machines is permitted. When working with the Hyperstack platform, you can easily set up firewall rules based on the three most commonly used Internet protocols: TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and ICMP (Internet Control Message Protocol). If your requirements involve more advanced protocols, you can use the Firewall APIs, which enable you to create firewalls based on an extensive list of protocols, catering to your unique networking needs.
In this article
Default firewall rules
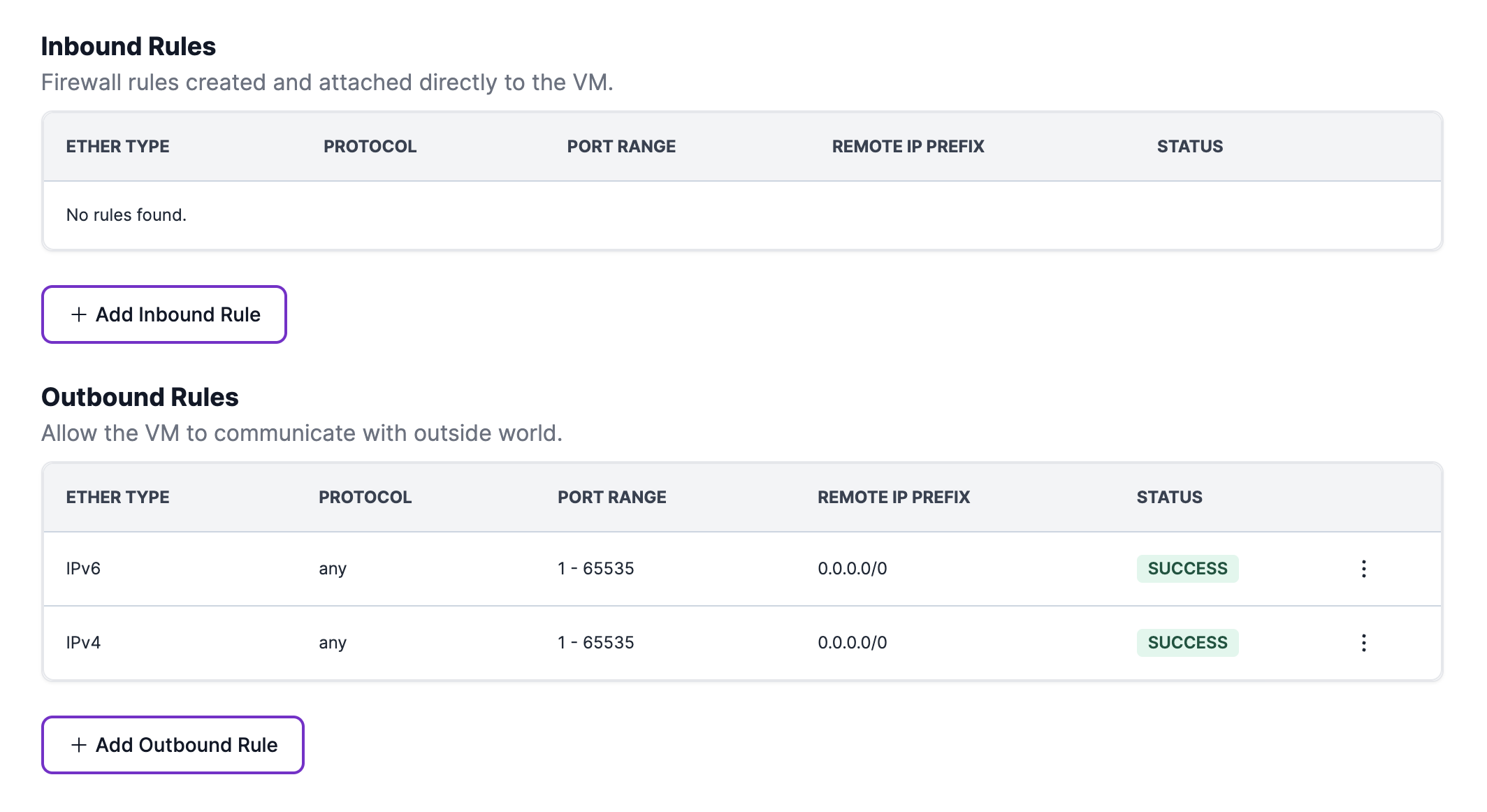
New virtual machines are secure by default, initially configured without any firewall rules allowing incoming traffic. To enable incoming traffic, users must create firewall rules tailored to their needs.
Additionally, virtual machines come with pre-configured firewall rules permitting outgoing IPv4 and IPv6 traffic using any internet protocol, on any port (1-65536), and to any destination IP address (0.0.0.0/0). If desired, these pre-configured firewall rules for incoming traffic can be deleted to restrict outgoing traffic.
Default virtual machine firewall rule configuration as shown in Hyperstack:
How to guides
Creating direct firewall rules
To create a firewall rule for a specific virtual machine, follow the steps shown below.
-
In Hyperstack, go to the 'My Virtual Machines' page to access your VMs. Click on the name of the VM you wish to create a firewall for to access its details.
-
Navigate to the Firewall tab on the VM's details page. Under the Direct Firewall Rules section, click + Add Inbound/Outbound Rule depending on your needs.
-
Complete the fields for the firewall rule, including:
a. Ether type: Select either IPv4 or IPv6.
b. Internet protocol: Choose TCP, UDP, or ICMP.
c. Port range: Specify the range of ports to allow (e.g., 1-65536).
d. Remote IP prefix: Enter the IP address for permitted traffic.
e. Click Add.
We recommend creating direct firewall rules only when you don't intend to use the same rule on other VMs. By creating a firewall with attached rules, you can apply the same configuration across multiple VMs. Follow the steps below to learn how to create a firewall.
Creating firewalls in Hyperstack
To create a firewall containing firewall rules that can be attached to any virtual machine, follow the steps below.
-
In Hyperstack, click on the Firewalls section located on the sidebar and click Create a new firewall.
-
Give your firewall a name and choose an environment to create it in. Optionally, provide a description.
-
Add firewall rules to your firewall by clicking Add New Inbound/Outbound rule depending on your needs.
-
Complete the fields for each firewall rule, including:
a. Ether type: Select either IPv4 or IPv6.
b. Internet protocol: Choose TCP, UDP, or ICMP.
c. Port range: Specify the range of ports to allow (e.g., 1-65536).
d. Remote IP prefix: Enter the IP address for permitted traffic.
e. Click Add. -
Repeat steps 3 and 4 for all the firewall rules you need.
-
You are now ready to attach this firewall to a virtual machine to apply its security configuration. To learn how, click here.
Attach firewall to a VM
To attach an existing firewall to a virtual machine and apply its associated firewall rules, follow the steps below.
-
In Hyperstack, click on the Firewalls section located on the sidebar and select Manage attached VMs.
-
In the popup window, check the boxes beside the VM names to which you want to apply the firewall, and click Save changes.
-
Verify the successful attachment of the firewall by navigating to the My Virtual Machines page, and clicking on the name of the VM to access its details.
-
Go to the Firewall tab on the VM's details page and look for the name of the firewall under the Attached Firewalls section.
Supported Internet protocols
Using the Hyperstack platform, you can easily configure firewall rules for your virtual machines for the three most common internet protocols: TCP, UDP, and ICMP.
TCP (Transmission Control Protocol)
TCP is a connection-oriented protocol used for reliable and ordered data transmission. It ensures that data sent from one system arrives intact and correctly ordered at the destination. This protocol is commonly used to allow inbound web traffic via HTTP/HTTPS and SSH access for administrators.
UDP (User Datagram Protocol)
UDP is a connectionless protocol that is fast and efficient. This protocol does not guarantee the delivery or order of packets, making it suitable for real-time applications. This protocol is commonly used to allow DNS requests.
ICMP (Internet Control Message Protocol)
ICMP is a network layer protocol typically used for diagnostic purposes. This protocol is commonly used to create firewall rules that permit ping requests, so that error messages can be received.
To view a comprehensive list of protocols along with their validation schemes, including corresponding ethertype and port restrictions, click the drop-down below:
See protocols and validation schemes
| Protocol | Ethertype | Ports |
|---|---|---|
any | None | None |
tcp | IPv4/IPv6 | 1 - 65535 |
udp | IPv4/IPv6 | 1 - 65535 |
icmp | IPv4/IPv6 | None |
ah | IPv4/IPv6 | None |
dccp | IPv4/IPv6 | 1 - 65535 |
egp | IPv4/IPv6 | None |
esp | IPv4/IPv6 | None |
gre | IPv4/IPv6 | None |
icmpv6 | IPv4/IPv6 | None |
igmp | IPv4/IPv6 | None |
ipip | IPv4/IPv6 | None |
ipv6-encap | IPv6 | None |
ipv6-frag | IPv6 | None |
ipv6-icmp | IPv6 | None |
ipv6-nonxt | IPv6 | None |
ipv6-opts | IPv6 | None |
ipv6-route | IPv6 | None |
ospf | IPv4/IPv6 | None |
pgm | IPv4/IPv6 | None |
rsvp | IPv4/IPv6 | None |
sctp | IPv4/IPv6 | 1 - 65535 |
udplite | IPv4/IPv6 | 1 - 65535 |
vrrp | IPv4/IPv6 | None |
When dealing with the icmp and ipv6-icmp protocols, it's important to note that the values for port_range_min and port_range_max correspond to ICMP type and ICMP code, respectively. These values should fall within the range of 0 to 255.
If your use case involves advanced protocols beyond TCP, UDP, or ICMP, use the firewall APIs. Detailed API reference for creating firewall rules with the Infrahub API can be found below.
Firewall APIs
Operations for managing virtual machine firewalls.
| Endpoint Name | URL | Description |
|---|---|---|
| List firewalls | GET /core/firewalls | Returns a list of your existing firewalls. |
| Retrieve firewall details | GET /core/firewalls/{id} | Retrieves the details for a firewall. |
| Create firewall | POST /core/firewalls | Creates a firewall. |
| Delete firewall | DELETE /core/firewalls/{id} | Deletes a firewall. |
| Add firewall rule to firewall | POST /core/firewalls/{firewall_id}/firewall-rules | Adds firewall rules to a firewall. |
| Remove firewall rule from firewall | DELETE /core/firewalls/{firewall_id}/firewall-rules/{firewall_rule_id} | Deletes a firewall rule from a firewall. |
| Attach firewall to virtual machines | POST /core/firewalls/{firewall_id}/update-attachments | Attaches a firewall to one or more virtual machines. |
Direct firewall rule APIs
A set of operations for creating and managing direct firewall rules for virtual machines.
| Endpoint Name | URL | Description |
|---|---|---|
| Add firewall rule to virtual machine | POST /core/virtual-machines/{id}/sg-rules | Adds a firewall rule to a virtual machine. |
| Delete firewall rule from virtual machine | DELETE /core/virtual-machines/{id}/sg-rules/{sg_rule_id} | Deletes a firewall rule from a virtual machine. |